Table Of Contents
- Table Of Contents
- Executive Summary
- High Level Technical Summary
- Static Analysis
- Interesting Strings
- Static Analysis Using Cutter (Kill Switch)
- Dynamic Analysis
- Indicators Of Compromise (IOCs)
- Host Based IOCs
- Disk Activity
- Persistence
- Dynamic Analysis using ProcMon
- Task Manager
- Network Based IOCs
- ProcMon Analysis
- Other Registry Changes
- Rules and Signatures
- Appendices
- Appendix B
- References
Executive Summary
The following are hashes of the main dropper executable.
| md5sum | db349b97c37d22f5ea1d1841e3c89eb4 |
| sha256sum | 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c |
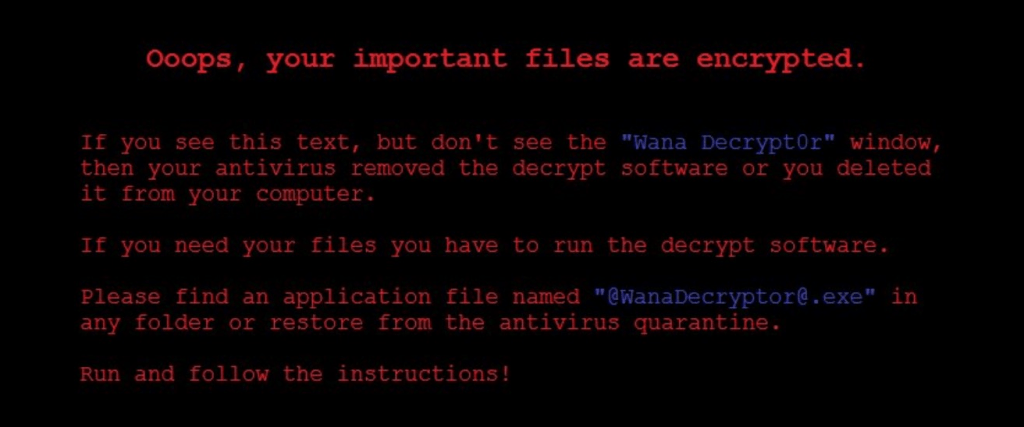
WannaCry is a ransomware cryptoworm which has the ability to encrypt files on an infected host and propagate through a network by itself. It attacked computers worldwide in 2017 until its march was stopped by a researcher named Marcus Hutchins who registered the kill-switch domain that causes the malware to simply exit. It is a C-compiled dropper that runs on and attacks computers running the Windows operating system. This malware is known to spread via exploiting the SMB EternalBlue flaw present on older versions of Windows.
Symptoms of infection include:
- Image files cannot be opened.
- The desktop background switches to a ransom message.
- Encryption of all files on the filesystem.
- A file named @WanaDecryptor@.exe shows up on the Desktop.
- A window (that cannot be removed) with instructions on how and by when to pay the ransom to get the files decrypted.
- A hidden directory named ldubjjytkvotzxy918 is created under c:\ProgramData.
YARA signature rules are attached in Appendix A. The sample hashes are available on VirusTotal for further examination

High Level Technical Summary
WannaCry has 3 components to it –
- a dropper (Ransomware.wannacry.exe or similar name),
- an encryptor(%WinDir%\tasksche.exe) and
- a decryptor (@WanaDecryptor@.exe).
It first tries to connect to a non-existent (originally) web domain (Appendix B) and quits if the host is contactable (kill switch). It probably does this to avoid running in a sandbox where it is likely to be analyzed. If the domain is not contactable, it begins execution. It persists itself by modifying a registry entry so that it can start running again if the machine restarts.
Static Analysis
Static analysis was performed using the Mandiant Floss program. Strings longer than 6 characters were dumped to a file and then examined using an editor.
floss -n 6 Ransomware.Wanncry.exe > wannacry.txtInteresting Strings
This is an unobfuscated Win32 binary. We see plenty of Win32 calls.
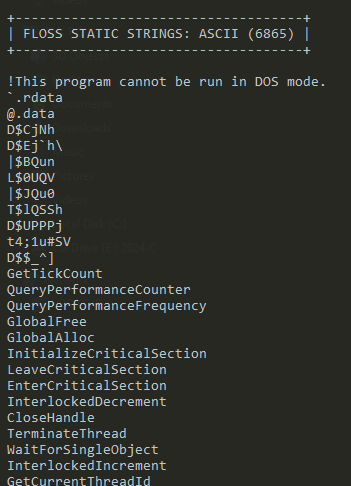
It imports iphlpapi.dll (IP Helper API) that exposes IP/Networking related APIs.
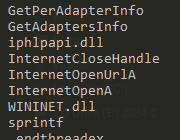
There is a reference to mssesecsvc.exe.
This check could be an anti-analysis feature.
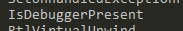
Perhaps the most interesting strings – Execution of a binary with -security, several references to c:\ and c:\Windows, tasksche.exe, file creation API calls and a suspicious looking URL
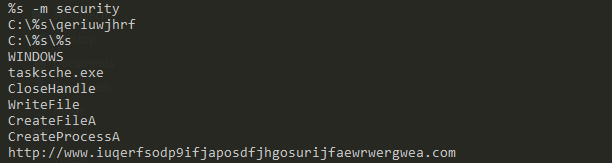
An indication that the malware is doing some encryption.

Another set of interesting strings – the WannyCry extension (.wnry), icacls ./grant (changing ACLs on files), attrib + h (hiding a file or directory), GetNativeSystemInfo (getting information about the system).

Some kind of locale specific behavior – with .wnry telltale giveaway.
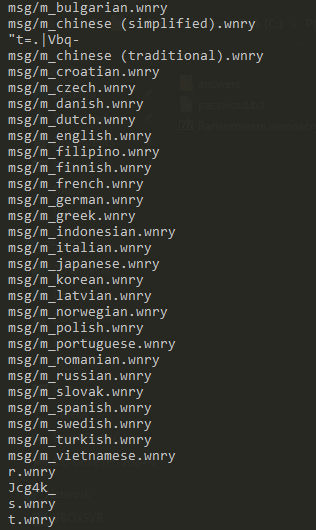
References to IP addresses

Long encoded strings

An assembly manifest
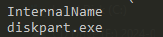
A suspicious reference to the system Disk Partition utility.
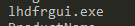
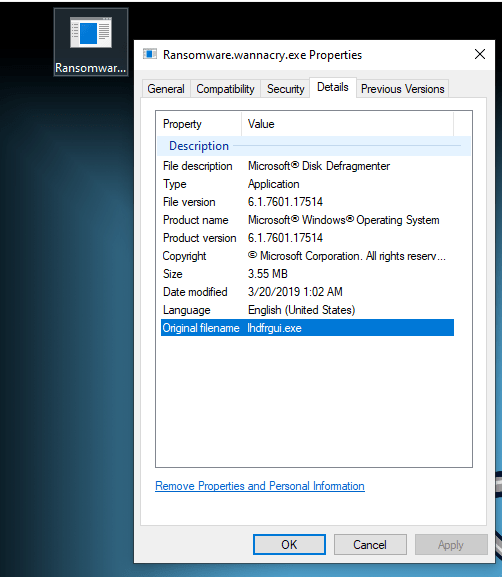
Another suspicious reference to a renamed dfrgui.exe – the Microsoft Disk Defragmenter.
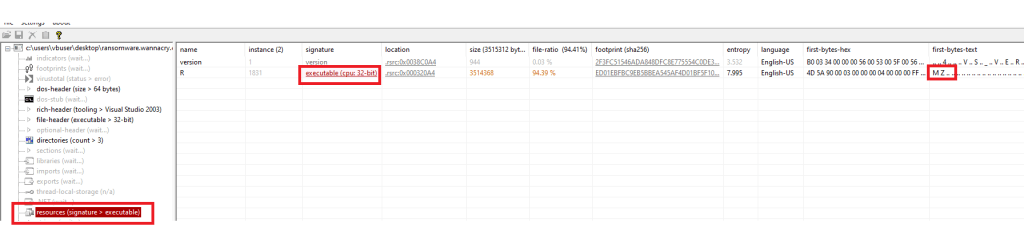
PE View displays an embedded executable (with the MZ magic header) hidden inside the resources section.
Static Analysis Using Cutter (Kill Switch)
When the malware binary is detonated with INetSim turned on, it simply exits. When detonated without INetSim (and with elevated privileges), it starts its work. We want to see where this logic is hidden in the malware.
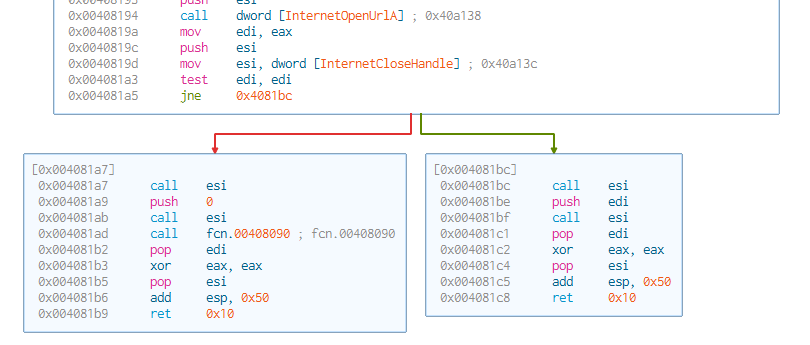
The code executes if the target host is inaccessible i.e. if InternetOpenUrlA returns a FALSE value.
EAX contains the return value of InternetOpenUrlA . This value is moved to EDI. EDI is then tested and the code either jumps to detonating the code (0x004081a7) or to exiting (0x004081bc) depending on this final value in EDI.
Dynamic Analysis
To start dynamic analysis, we detonate the malware as admin on the sandbox. We also start the SysInternals TcpView program. We notice several new files appearing on the Desktop.
Indicators Of Compromise (IOCs)
Host Based IOCs
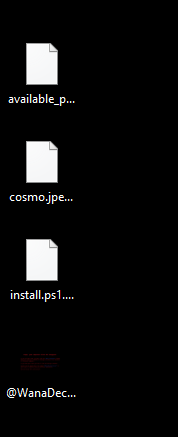
Files created on the host after malware detonation.

The malware binary’s original file name attribute is set to allow it to masquerade as a legal Windows binary a.k.a. the Windows Disk Defragmenter.
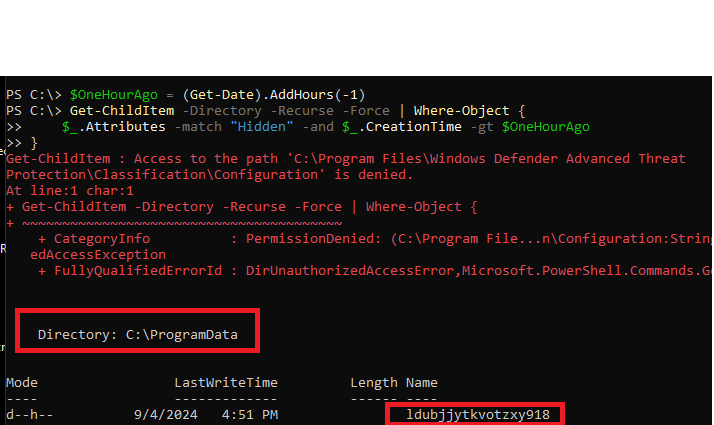
Disk Activity
Any malware is likely to have written some not-so-easy-to-find artefacts to the disk. Let use PowerShell to look for hidden folders created in the last 1 hour on the C:\ drive.
$OneHourAgo = (Get-Date).AddHours(-1)
Get-ChildItem -Directory -Recurse -Force | Where-Object {
$_.Attributes -match "Hidden" -and $_.CreationTime -gt $OneHourAgo
}Run in an elevated powershell terminal in c:\
We see a new hidden directory named ldubjjytkvotzxy918 created under c:\ProgramData.
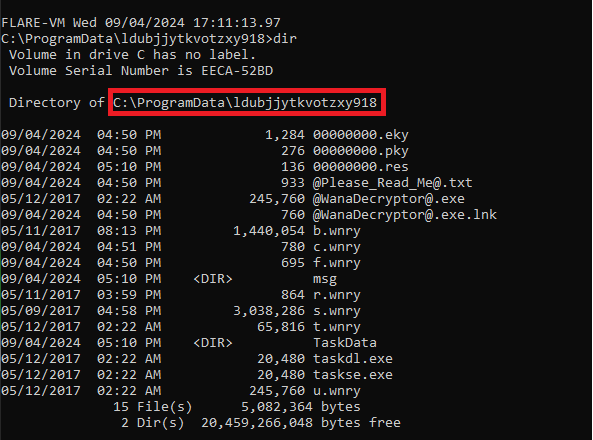
Several of the file names listed here were discovered during static analysis.
Persistence
The malware writes an entry into the Windows Registry under HKLM:SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run. This allows it to persist across machine restarts.

Dynamic Analysis using ProcMon
We filter on ProcessName contains “wanna”.
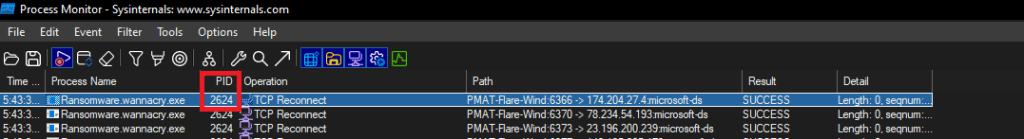
The ProcMon Process Tree for the process shows the malware running disguised as “Microsoft Disk Fragmenter”.

The main process launches 3 other processes i.e. tasksche.exe, taskdl.exe and taskse.exe. Recall the presence of these executables in the hidden directory created on the C:\ drive.
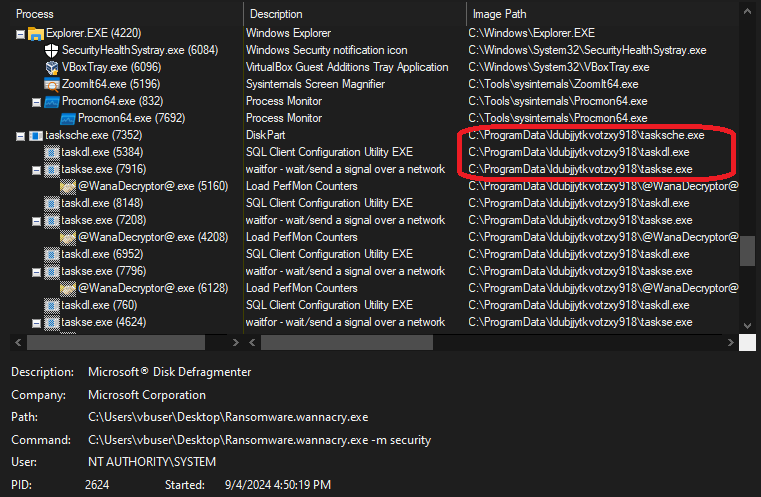
The creation of the files in the hidden directory is displayed when we filter on CreateFile operations and Path containing ldubjjytkvotzxy918.

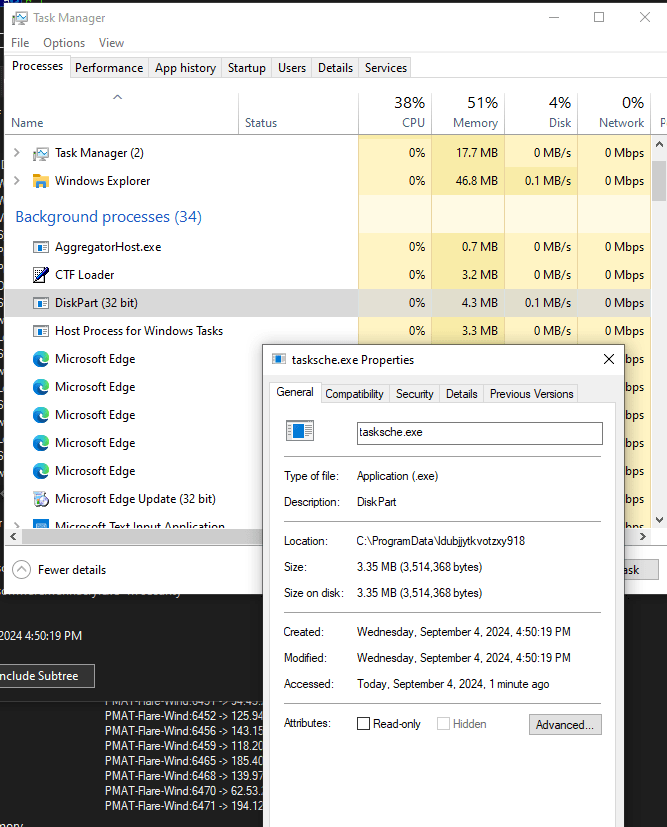
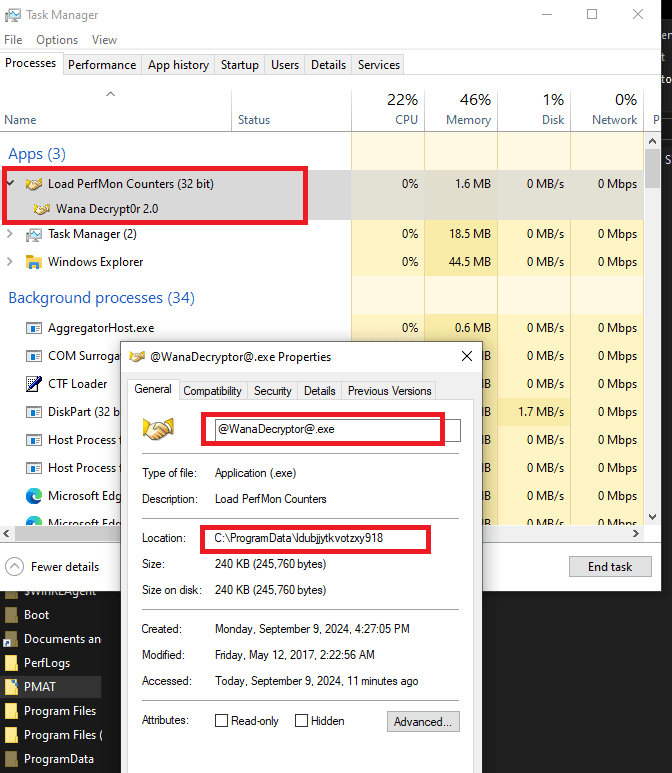
Task Manager
There is a background process that runs the encrypter (tasksche.exe). It is named “DiskPart.exe” to avoid immediate visual detection.
We also see a process named “taskhsvc.exe” which actually points towards the Tor browser binary in the malware directory.
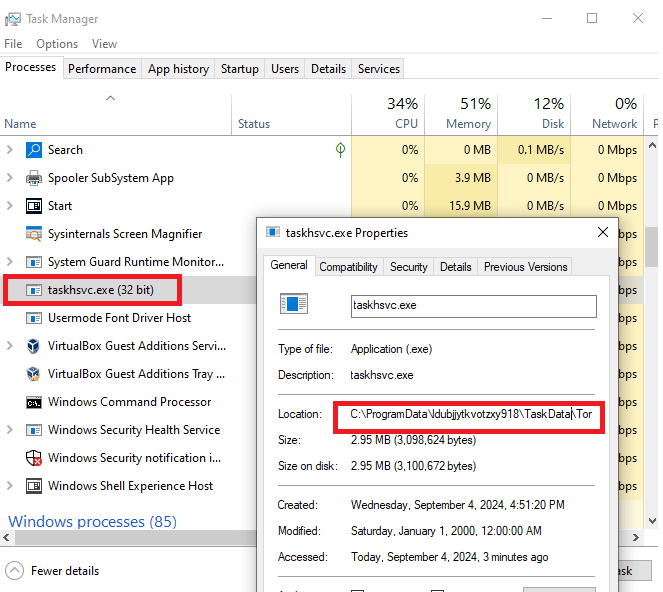
We also notice a Windows service with the same name as the malware directory. This points to the same binary as the encrypter component of the malware.

We can verify that this service has been registered in the Registry under HKLM:\SYSTEM\ControlSet001\Services.
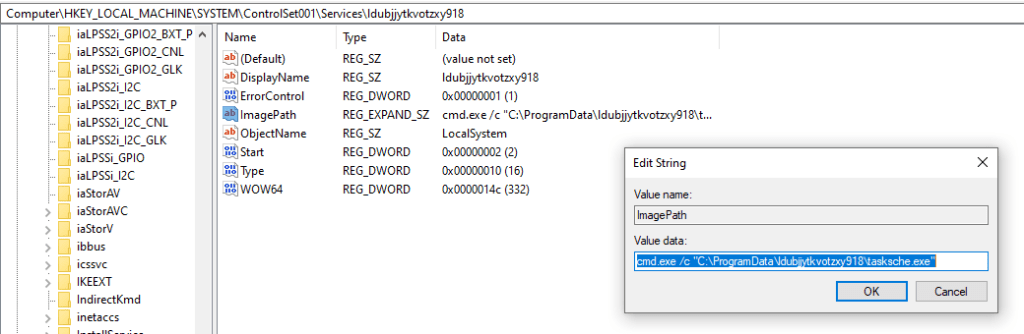
The decryptor component of the malware is seen below. This component displays the window that displays ransomware payment information.
Network Based IOCs
We start INetSim on the analysis machine and detonate the malware, we see a DNS request going out to the kill-switch domain. Since INetSim returns a OK response, the malware exits without doing any damage.

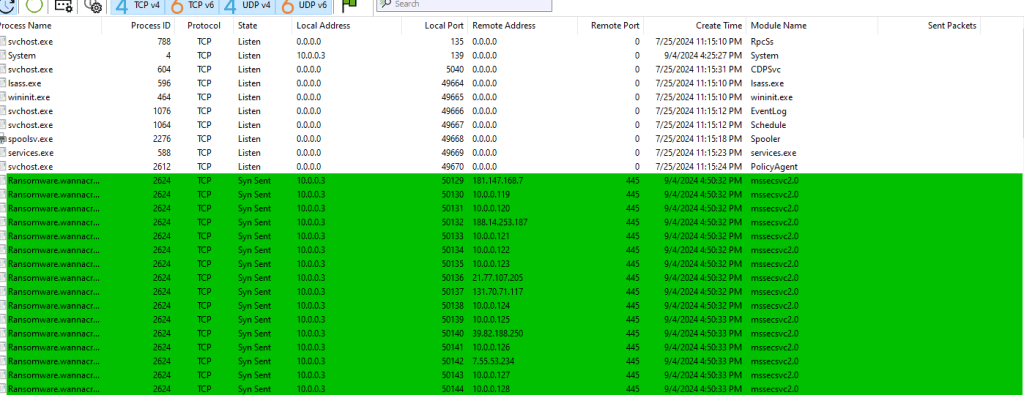
We use TcpView to watch network activity. When we detonate the malware without starting INetSim, and monitor the network traffic on the analysis machine, we see the malware trying to connect to a bunch of hosts on port 445 (SMB).
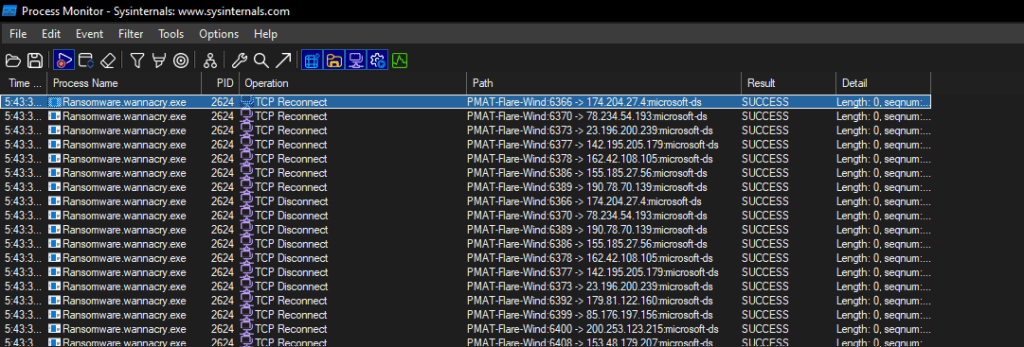
ProcMon Analysis
Lets start by filtering on the name of the executable => ProcessName contains “wanna”. We see the malware attempting network connections to several IPs. This validates the traffic seen in the TcpView output above.
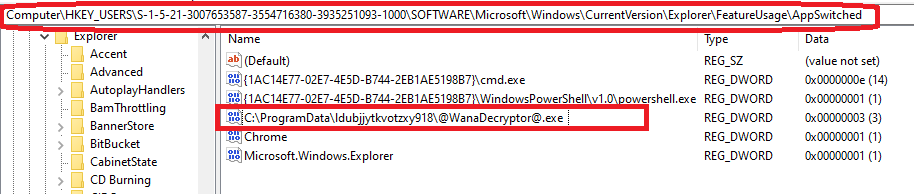
Other Registry Changes
This key represents the number of times an application switched focus (was left-clicked on the taskbar). It shows the number of times the WanaDecryptor was minimized or maximized, as opposed to just launched.
The exact use of this registry entry is not clear at the time this report was first written.
Rules and Signatures
A YARA rule to detect the dropper executable is included in Appendix A.
Appendices
Appendix A
The following Yara rule can be used to detect the presence of the ransomware dropper executable on the infected machine. The complete rule can be accessed from https://github.com/raghavanks/pmat/blob/3c221454fa7717d44f9f3b8ce28c3850480b3c6e/wannacry.yara.
rule PMATDetectWannaCry {
meta:
last_updated = "2024-09-08"
author = "Raghavan"
description = "A Yara rule for WannaCry based on strings found during static analysis."
strings:
// Fill out identifying strings and other criteria
$s1 = "iphlpapi.dll" ascii // match this ascii string
$s2 = "mssecsvc.exe"
$s3 = "cmd.exe /c"
$s4 = "icacls . /grant Everyone"
$s5 = "r.wnry"
$s6 = "tasksche.exe"
$s7 = "http://"
$pe_magic_byte = "MZ" // PE magic byte
$sb64="fd4d9L7LS8S9B/wrEIUITZWAQeOPEtmB9vuq8KgrAP3loQnkmQdvP0QF9j8CIF9EdmNK3KEnH2CBme0Xxbx/WOOCBCDPvvjJYvcvf95egcjZ+dWquiACPOkTFW3JS6M+sLa/pa6uVzjjWOIeBX+V3Pu12C9PjUWOoRfFOAX+SFzVJL4ugpzxsVRvgFvIgqXupq+y6bfWsK90pWeE5qzBSTKcSepm0GPGr/rJg0hJn4aVBbsdnXxM2ZCDorVUsFUsF9vXC2UIJlsx5yEdThqQ5MoEd6tRwRSfYA87dvMJrPfpB8qLIaFHNX684tJJn30Bx0vnkLW3oRcGKuBqZdJ/PI4yIm++QVKkBLVa106S2gpwejplTs510cW0VN+8yVJAuZhPZSij7FLlAE4zS0bjSo6lP098nSduB9h9eziOeLhd1KG16h+g8xP2CV1VsNhr9ao+2cmCeiHYhbceDilST+ASGztHMWarFIlJUL6qlCrptzEJTk+er2j7SfHHT0nNtEa4+JRvPq5C21Kd1pcQ7vKlvZ5flQs1vvXTGZhYZKTv5lrdWNEtVEzGh+KvTFJxqKz5LNvLPT/0yRqcO6deL/nmv3UCt+B0Ut2X6cNonJG76Ut78wcRv4YP2MwApDS9fSz2AGGVxm246qiUiKWWtM6w40aDjuPH7gCQEoDHwhJgvLgmSaibPwjJrDzO0hMGDrp6SxwIFNS1G2oAPcvOn4CL4JDuLCBs08NtDrQysl0WMgCIBM+1O5D8Lue0J0359/4fCzqNCvBoqgyss9YWZb6wy6C/Kz4ak/Qmt74uXsA71fduIs3zEs6CAPpQQlvXMlZYWczpenAS2b+gO6aHHEFZBJmJ6Vy9I4RoLIPH/8Ig1ManJzkgPODvGvcuE/WUDFmiIiwGMlFMFTchBTVUQSPaLFWMUk6FqeO1LTY2/Rc3lSWSuBVeAAtlUNa6kfXqh/9=="
condition:
// Fill out the conditions that must be met to identify the binary
$pe_magic_byte at 0 and // PE magic byte at 00
all of ($s*) // all strings starting with s.Appendix B
The following URLs show up in the static analysis phase. \171.16.99.5\IPC$ and \192.168.56.20\IPC$.
The following URL http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com is the kill switch that if accessible, causes the malware to exit without doing its damage.
Leave a comment